6. Kubernetes: SecurityContexts
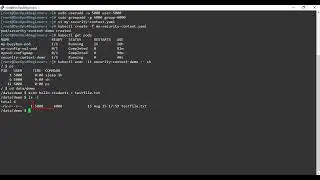
sudo useradd -u 5000 user-5000
sudo groupadd -g 6000 group-6000
**** Example:01 ****
vi my-security-context.yaml
apiVersion: v1
kind: Pod
metadata:
name: security-context-demo
spec:
securityContext:
runAsUser: 5000
fsGroup: 6000
volumes:
name: sec-ctx-vol
emptyDir: {}
containers:
name: sec-ctx-demo
image: busybox
command: [ "sh", "-c", "sleep 1h" ]
volumeMounts:
name: sec-ctx-vol
mountPath: /data/demo
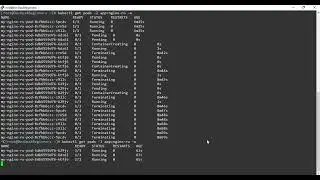
kubectl create -f my-security-context.yaml
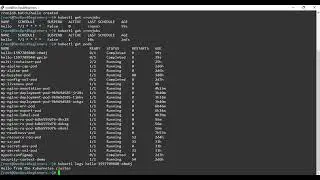
kubectl get pods
kubectl exec -it security-context-demo -- sh
ps
cd data/demo
echo hello students # testfile.txt
ls -l
**** Example:02 ****
vi my-alpine.yaml
apiVersion: v1
kind: Pod
metadata:
name: my-alpine-pod
spec:
containers:
name: my-alpine-container
image: alpine
command: ["/bin/sleep", "999999"]
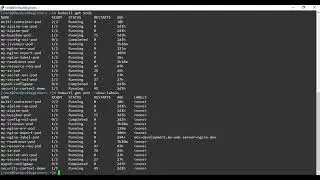
kubectl create -f my-alpine.yaml
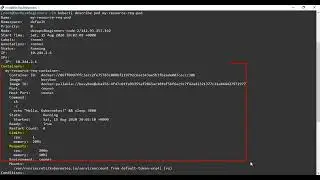
kubectl exec -it my-alpine-pod -- sh
date +%T -s "11:14:00"
ls -la
chown 5000:6000 bin
**** Example:03 ****
vi my-capababilities.yaml
apiVersion: v1
kind: Pod
metadata:
name: my-alpine-cap-pod
spec:
containers:
name: my-alpine-cap-container
image: alpine
command: ["/bin/sleep", "999999"]
securityContext:
capabilities:
add:
SYS_TIME
drop:
CHOWN
kubectl create -f my-capababilities.yaml
kubectl exec -it my-alpine-cap-pod -- sh
date +%T -s "11:14:00"
ls -la
chown 5000:6000 bin

![[AMV] верно, я Кира..](https://images.videosashka.com/watch/8-3v0E_Axvw)