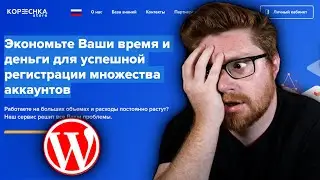
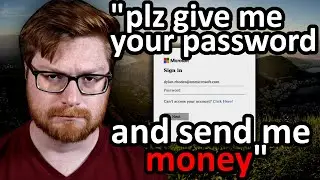
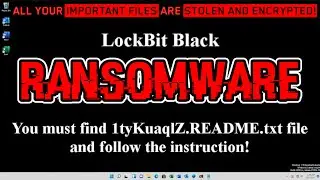
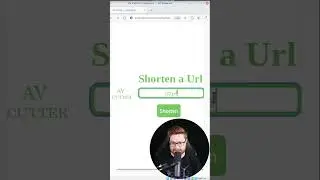
I Can't Scan This Website
https://jh.live/cloakingfirewall || Check out the Cloaking Firewall to protect your infrastructure, and test it with either with a local ISO, cloud AWS image, or their public demo! https://jh.live/cloakingfirewall
Learn Cybersecurity - Name Your Price Training with John Hammond: https://nameyourpricetraining.com
Learn Coding: https://jh.live/codecrafters
WATCH MORE:
Dark Web & Cybercrime Investigations: • Tracking Cybercrime on Telegram
Malware & Hacker Tradecraft: • Malware Analysis & Threat Intel: UAC ...
📧JOIN MY NEWSLETTER ➡ https://jh.live/email
🙏SUPPORT THE CHANNEL ➡ https://jh.live/patreon
🤝 SPONSOR THE CHANNEL ➡ https://jh.live/sponsor
🌎FOLLOW ME EVERYWHERE ➡ https://jh.live/twitter ↔ https://jh.live/linkedin ↔ https://jh.live/discord ↔ https://jh.live/instagram ↔ https://jh.live/tiktok
💥 SEND ME MALWARE ➡ https://jh.live/malware
🔥YOUTUBE ALGORITHM ➡ Like, Comment, & Subscribe!