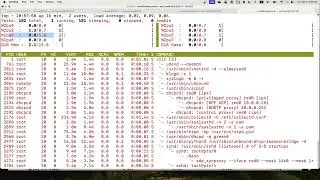
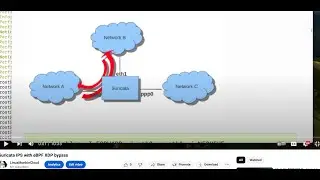
Suricata IPS with eBPF XDP bypass
Suricata has eBPF XDP bypass feature to allow some connection flow with big web payload content to bypass the Suricata detection, Here is how to configure and test that feature
af-packet:
interface: eno1
threads: auto
cluster-id: 99
cluster-type: cluster_qm #for IPS
cluster-type: cluster_flow #for IDS
defrag: yes
copy-mode: tap
copy-mode: ips
copy-iface: eno2
xdp-mode: driver
pinned-maps: true
pinned-maps-name: flow_table_v4
xdp-filter-file: /usr/libexec/suricata/ebpf/xdp_filter.bpf
bypass: yes
use-mmap: yes
ring-size: 200000
buffer-size: 64535
interface: eno2
threads: auto
cluster-id: 100
cluster-type: cluster_qm
defrag: yes
copy-mode: ips
copy-iface: eno1
xdp-mode: driver
pinned-maps: true
pinned-maps-name: flow_table_v4
xdp-filter-file: /usr/libexec/suricata/ebpf/xdp_filter.bpf
bypass: yes
use-mmap: yes
ring-size: 200000
buffer-size: 64535

![[AMV] верно, я Кира..](https://images.videosashka.com/watch/8-3v0E_Axvw)