Unpack Shellcode w/ Ghidra Emulator | Decode XOR Dynamically🔥
Here's the deal. We've been asked to Reverse Engineer this program called 'payload'. It does nothing when we run it... but... in the background, it is calling back to someone's Kali Linux machine and they have an open shell.
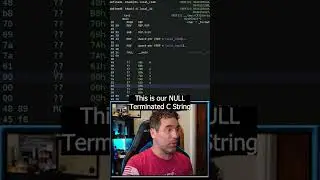
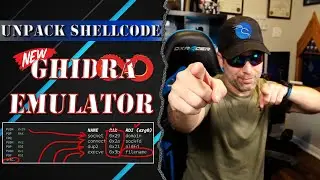
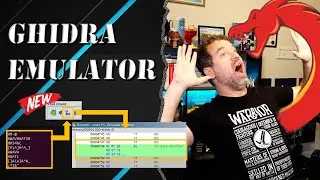
Yet, when we throw it into Ghidra, we are greated with an "Bad Instruction" message and a do-while loop that performs an XOR through-out the entirety of the executable. We're blind.
We will be following along with Craig Young's Blog Post to find out the best way to reverse engineer and unpack the embeded shellcode!
Enough talking, let's get hacking!
Unpacking Shellcode with Ghidra Emulator
/ unpacking-shellcode-with-ghidra-emulator
NVIDIA Broadcast 1.4 Eye Contact Effects
https://www.nvidia.com/en-us/geforce/...
0:00 Intro
0:23 Summary
2:22 Payload Generation
6:12 CodeBrowser Static Analysis
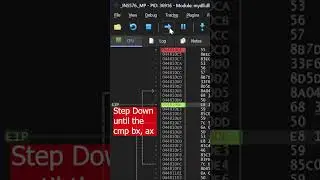
8:43 Emulator Dynamic Analysis
15:16 Exporting Decoded Data
17:17 Automatic Analysis of System Calls
22:22 Manual Analysis of System Calls
25:42 Conclusion









![[SCAM] I CAN'T BELIEVE HE'S DEAD | Fatal Crash Facebook Scam](https://images.videosashka.com/watch/yEuAolxdj0k)