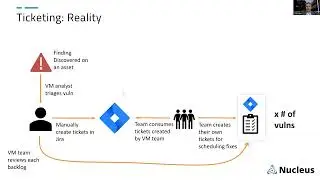
Asset Metadata Automation Deep Dive
In Episode 25 of Nucleus Shortcuts, our host Adam Dudley speaks to Aaron Attarzadeh, Field Security Engineer at Nucleus, all about Asset Metadata Automation.
Want to learn more about how Nucleus can help with vulnerability management? Check out our website: www.nucleussec.com