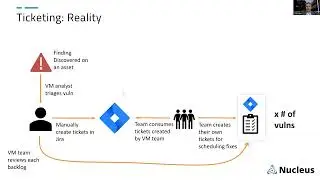
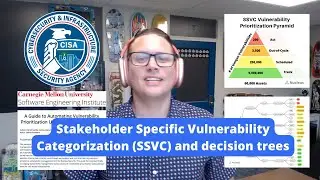
Visualizing Vulnerability Data with Patrick Garrity on Nucleus Shortcuts
In this episode of Nucleus Shortcuts, our host Adam Dudley sits down with Patrick Garrity, VP and Vulnerability Researcher at Nucleus Security, to talk about Visualizing Vulnerability Data and some of his recent visualizations.
Learn more about Nucleus at www.nucleussec.com





![CALLIGRAPHY ON IPAD TABLET [Arabic script on an abstract background]](https://images.videosashka.com/watch/Uu6CVlzLGhA)