Suricata Intrusion Detection System (IDS) with XDP DDOS protection
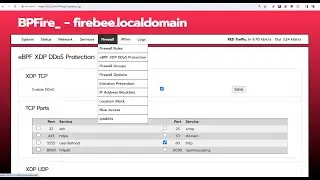
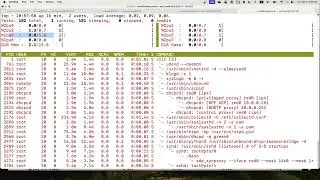
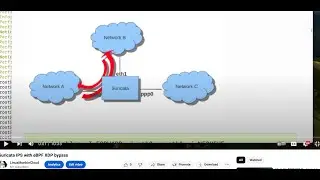
In this video, I added XDP DDOS protection to Suricata Intrusion Detection System to block SYN flood DDOS attack before the attack get into Suricata, without the DDOS protection, Suricata enter into emergency mode and consumes over 100% CPU, and it shows another way to attach multiple XDP program to same network interface with the xdp-project libxdp library.
af-packet:
interface: eno2
threads: auto
cluster-id: 99
cluster-type: cluster_qm # for IPS
cluster-type: cluster_flow # for IDS
defrag: yes
copy-mode: tap
copy-iface: eno2
xdp-mode: soft
pinned-maps: true
pinned-maps-name: flow_table_v4
xdp-filter-file: /usr/libexec/suricata/ebpf/xdp_filter.bpf
xdp-filter-prio: 100
xdp-syncookie-file: /usr/libexec/suricata/ebpf/xdp_synproxy_kern.bpf
xdp-syncookie-prio: 50
use-mmap: yes
ring-size: 200000
buffer-size: 64535
also need to setup netfilter connection tracking for good client
sysctl -w net.ipv4.tcp_syncookies=2
sysctl -w net.ipv4.tcp_timestamps=1
sysctl -w net.netfilter.nf_conntrack_tcp_loose=0
iptables -t raw -I PREROUTING -i eno2 -p tcp -m tcp --syn --dport 80 -j CT --notrack
iptables -t filter -A INPUT -i eno2 -p tcp -m tcp --dport 80 -m state --state INVALID,UNTRACKED -j SYNPROXY --sack-perm --timestamp --wscale 7 --mss 1460
iptables -t filter -A INPUT -i eno2 -m state --state INVALID -j DROP
#Suricata #IDS #eBPF #XDP #DDOS