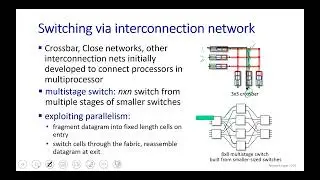
Network Protocols- How to install Telnet on Kali and capture login credentials
#protocol #attacks #hacking #telnet
In this video you will learn
1- What is the purpose of Telnet protocol
2- How to install and configure telnet server on Kali
3- How to capture telnet login and password.