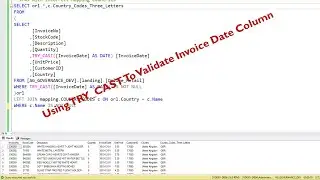
Securing sensitive information in AWS Secret Manager and Retrieving in AWS Lambda Dynamically
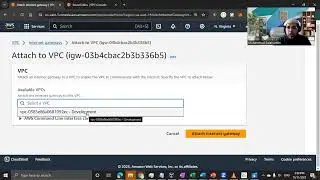
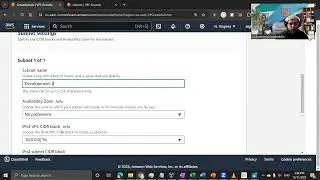
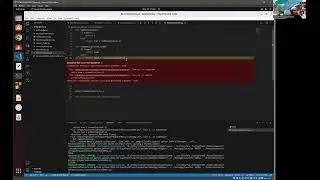
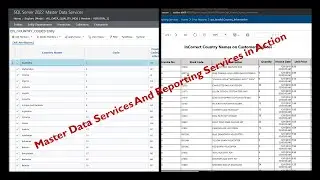
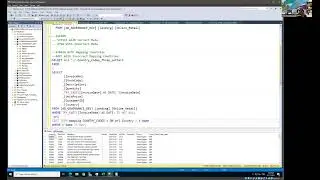
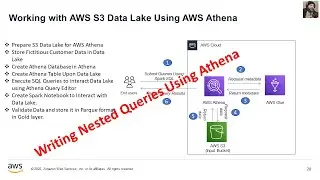
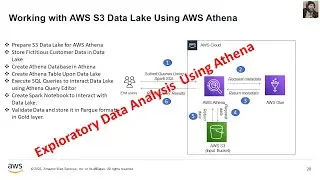
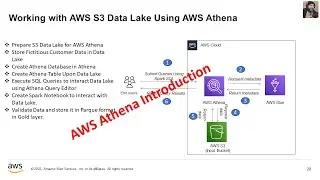
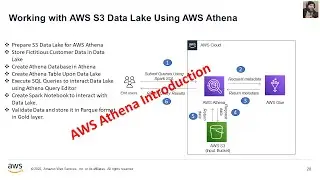
This marks the concluding video in the series, where we place emphasis on the storage and retrieval of sensitive data from AWS Secret Manager. Furthermore, I've undertaken a revision of the architectural diagram's process flow to enhance the comprehension of the holistic solution.

![[FREE] SLIMESITO x BEEZYB TYPE BEAT 2022 -](https://images.videosashka.com/watch/1EoTITwenvE)