Configuring a Zone-Based Policy Firewall (ZPF), P.T. v.7.2
https://www.youtube.com/user/MrSaleh9...
download packet tracer's source file:
https://drive.google.com/file/d/1e3nh...
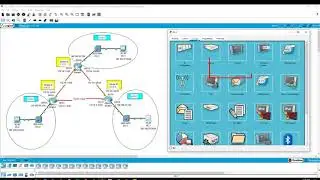
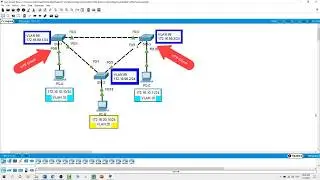
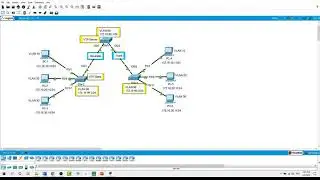
ZPF: Zone-based Policy Firewall
• Configuring a firewall on Router3.
• Verifying connectivity using SSH, Ping and the web browser.
ZPFs are the latest development in the evolution of Cisco firewall technologies, we will configure a basic ZPF on Router3 that allows internal hosts access to external resources and blocks external hosts from accessing internal resources, then we will verify firewall functionality from internal and external hosts.
• Configure static route between the routers.
- Verify connectivity by pinging PC-A from PC-1
- Access Router2 using SSH.
- From PC-! Open a web browser to the PC-A server.
• Let us issue this command on Router3 to view the technology package license information.
show version and if it has not been enabled, we will use this command to enable it.
license boot module c1900 technology-package securityk9
- Accept the end-user license agreement, save the running-config and then reload the router to enable the security license.
- show version to verify that it has been enabled.
• Use the zone security command to create a zone named IN-ZONE
- zone security IN-ZONE
- exit
• Create an external zone named OUT-ZONE
zone security OUT-ZONE
exit
• Now we need to identify the traffic using a class-map, but first we will create an ACL that defines the internal traffic, we will create an extended ACL 101 to permit all IP protocols from the network of 192.168.3.0/24 source network to any destination
access-list 101 permit ip 192.168.3.0 0.0.0.255 any.
• Now we will create a class map referencing the internal traffic ACL , here I will use the class-map type inspect command with the match-all option to create a class map named IN-NET-CLASS-MAP, then use the match class-group command to match ACL 101.
class-map type inspect match-all IN-NET-CLASS-MAP
match access-group 101
exit
• Now we will specify the firewall policies, by creating a policy map to determine what to do with matched traffic, I will use the policy-map type inspect command and create a policy map named IN-2-OUT-PMAP
policy-map type inspect IN-2-OUT-PMAP
• Now Specify class type of inspect and reference class map IN-NET-CLASS-MAP
class type inspect IN-NET-CLASS-MAP
• Now we will specify the action of inspect for this policy map by using the command inspect this invokes context-based access control, the other options are ( pass and drop).
inspect
It will tell us here that we didn’t specify a protocol in our class map so it will inspect all protocols.
exit twice.
• Now it is time to apply the firewall policies by creating a pair of zones by using the zone-pair security command, I will create a zone pair named IN-2-OUT-ZPAIR, and specify the source and destination zones that we created earlier, and IN zone and the OUT zone.
zone-pair security IN-2-OUT-ZPAIR source IN-ZONE destination OUT-ZONE
• Now I will specify the policy map for handling the traffic between the two zones, by attaching the policy map and it’s associated actions to the zone pair using the service-policy type inspect command and reference the policy map previously created PMAP
service-policy type inspect IN-2-OUT-PMAP
exit
• Now we will assign interfaces to the appropriate security zones by using the zone-member security command interface configuration mode to assign the interface on G0/1 IN-ZONE and S0/0/1 to OUT-ZONE
interface G0/1
zone-member security IN-ZONE
exit
interface s0/0/1
zone-member security OUT-ZONE
exit
• Now I will test the firewall functionality from IN to OUT, let us see if the internal hosts can still access external resources after this configurations, from PC-1, Ping the PC-A server
ping 192.168.1.3 it should be successful
- From PC-1 SSH to Router2 at 10.2.2.2, it should be successful
- Issue the command
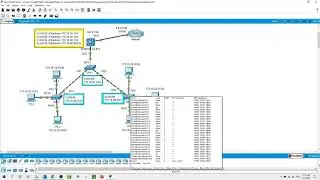
show policy-map type inspect zone-pair sessions on Router3
- What is the source IP address and port #
- What is the destination IP address and port # ?
• From PC-1 open a web browser to the PC-A server web page, and while the HTTP session is active, run this command:
show policy-map type inspect zone-pair sessions on Router3
- What is the source IP address and port #?
- What is the destination IP address and port# ?
• Now let us test the firewall functionality from OUT to IN zones.
- Let us verify that the external hosts can’t access internal resources after configuring the ZPF.
- From PC-A server ping PC-1, the ping should fail.
ping 192.168.3.3
- From Router2 ping PC-1, the ping should fail
ping 192.168.3.3