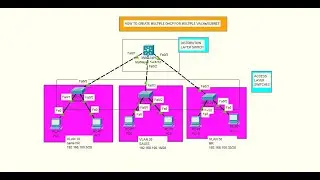
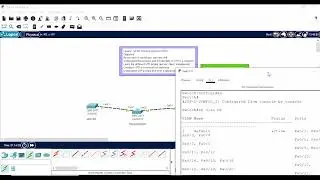
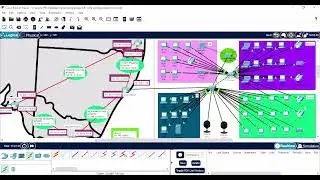
SSH (Secure Shell) Configuration on Cisco Packet Tracer || Step-by-step Guide
SSH stands for Secure Shell, a network protocol and cryptographic technology used to secure communication over a potentially unsecured network. SSH is commonly used for secure remote access to computer systems, allowing users to log in to remote servers or devices over a network, execute commands on them, and transfer files securely.
Here are some key aspects of SSH:
Authentication: SSH uses a combination of public key cryptography and passwords for user authentication. Public key cryptography allows users to generate a pair of keys: a public key (shared) and a private key (kept secret). When connecting to an SSH server, the client and server use these keys to authenticate each other. This is considered more secure than traditional password-based authentication.
Encryption: SSH encrypts the data transmitted between the client and server, including login credentials, commands, and data transfers. This encryption ensures that even if someone intercepts the network traffic, they cannot easily decipher the information being sent.
Remote Shell Access: One of the primary uses of SSH is to provide secure shell access to remote servers. Users can log in to a remote system and execute commands as if they were physically present at the machine.
Secure File Transfer: SSH also supports secure file transfers using tools like SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol). This lets users securely upload and download files to and from remote servers.
Port Forwarding: SSH can be used to create secure tunnels for port forwarding, allowing users to access services running on a remote server as if they were on the local machine. This is useful for securely accessing databases, web applications, or other services hosted on remote servers.
SSH is widely used in the IT industry for managing remote servers, configuring network devices, and securing communication between systems. It has become an essential tool for system administrators, developers, and anyone who needs to work with remote systems securely.
#CiscoPacketTracer
#Networking
#SSH #SecureSherll #Telnet #networksecurity