Logging PuTTY SSH sessions on Microsoft Windows 10 client GPO - group policy registry
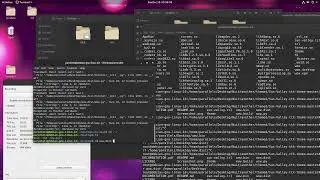
One could use PuTTY and some crafty scriptery to ensure a call to 'ssh someuser@somehost' is logged in entirety to an auditing/logging area.
putty $args[0]
&Y-&M-&D-&T.log
You could pair this with Logstash-Forwarder or Filebeat to start shipping logs and perhaps trip alarms on use of nmap, or perhaps access to /etc/shadow and other such unique behavior that might make an old man spill coffee.
We will make use of client GPO - group policy registry config updates.