Splunk TCPDUMP honeypot forward Linux terminal commands output
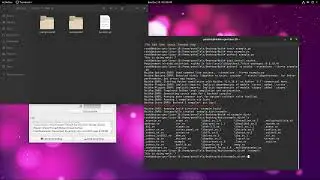
This is how you setup a tcpdump honeypot using Splunk's universal forwarder. This is going to allow you to perform field extractions and you could check for a particular IP address having multiple different port checks for example, highly likely indicating port scans.
This is a very basic and simple honeypot-of-sorts, because all we are doing is reporting to Splunk any ports of interest being called to. What ports you listen to is up to you, as well as any hosts you ignore for example vulnerability scanner servers:
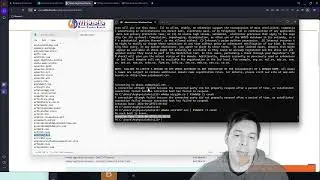
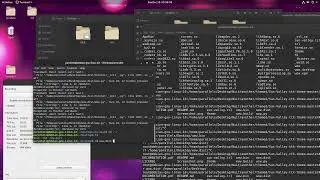
sudo tcpdump -tttt -q -l -i eth0 -n -s0 port 443 and not net 20.150.32.36/32 (output right arrow char.. just check pastebin link) eww&
disown
Pastebin: https://pastebin.com/5AB7sL4u
That will leave the tcpdump process running to write to that file.
I'd recommend setting a cron to gut that file every so often, log rotation, or just anything. Please post in the comments if you need help - any questions I am happy to assist with! There is no dumb question.