How to secure your Linux server
Looking to improve your Linux security and protect your server from attacks? In this video, we walk you through essential Linux hardening steps to enhance your Linux endpoint security and prevent unauthorized access. Whether you're managing a VPS or a dedicated machine, these best practices for Linux server hardening will help you secure your system in just a few minutes.
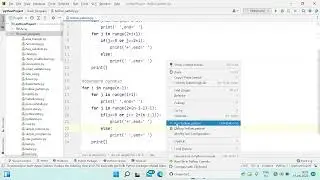
You’ll learn how to update your server, disable root login, set up SSH keys, configure a firewall with UFW, and use Fail2Ban to block brute-force attempts. We’ll also show you how to monitor system logs for suspicious activity, run malware scans, and create reliable backup strategies using rsync and Object Storage.
For advanced protection, we cover how to automate backups or enable Contabo’s Auto Backup feature for peace of mind.
🕐 Timeline:
0:00 - 0:21 Introduction to Linux security
0:21 - 0:34 Update your Linux system (Linux hardening begins)
0:34 - 1:08 Disable root login & set up SSH keys (Linux server hardening)
1:08 - 1:21 Configure firewall with UFW (Linux endpoint security)
1:21 - 1:49 Prevent brute-force attacks with Fail2Ban
1:49 - 2:34 Monitor logs & respond to suspicious activity
2:34 - 3:10 Set up local & remote backups (Object Storage, Auto Backup)
3:10 - 3:37 Conclusion
Key Topics Covered:
Updating your Linux server to fix known security vulnerabilities
Disabling root login and securing SSH access with key-based authentication
Setting up a firewall (UFW) and using Fail2Ban
Monitoring login activity via system logs and responding to suspicious behavior
Creating and automating secure backups with rsync or Object Storage solutions
Applying essential Linux server hardening practices for improved endpoint security
Important Notes:
Keep your Linux system fully updated to patch security vulnerabilities
Disable root login and use SSH keys instead of passwords for safer access
Set up a firewall (e.g., UFW) to allow only necessary ports
Install Fail2Ban to block brute-force SSH attacks automatically
Regularly monitor login logs and remove unauthorized SSH keys if found
Always maintain automated or regular backups to recover from breaches or data loss
Visit our website: https://contabo.com
Support Center: https://contabo.com/support
#linuxsecurity #linuxhardening #linuxserver #fail2ban #contabo #endpointsecurity #sshsecurity #linuxfirewall #linuxadmin #serverprotection





![CALLIGRAPHY ON IPAD TABLET [Arabic script on an abstract background]](https://images.videosashka.com/watch/Uu6CVlzLGhA)