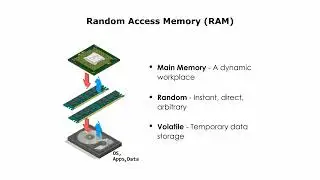
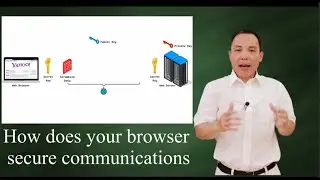
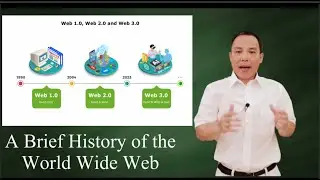
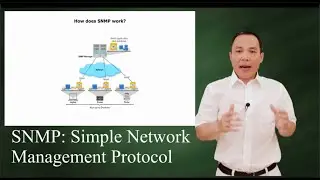
The ElGamal Algorithm: a simple example
Last time I talked about the three-step process of the ElGamal algorithm and how it works in math formulas. Today I will demonstrate how it works with a simple example – using these formulas and showing the ElGamal works.
Playlists:
Basic Cryptography
• Private Key Encryption (Symmetric Key...
Advanced Cryptography:
• What is digital signature?
Public Key Infrastructure
• Why digital certificate?
Privacy Enhanced Technologies
• Surface net, Deep net, and darknet
Business continuity
• Business continuity
Cyber Attacks and Defense
• AAA framework: TACACS+ vs RADIUS
Remote Access & WAN Technologies
• Circuit Switching vs. Packet Switching
![»No way-- Gacha HP AU/UA meme/trend not og [Pansy, Hermione and Ron]](https://images.videosashka.com/watch/cQeCV6F0nyg)





![[FREE] JUICE WRLD x SOFAYGO TYPE BEAT 2023 -](https://images.videosashka.com/watch/mhM6Knmx16c)