Zerotrust
3:43

Zero Trust Explained in 4 mins
A zero trust approach aims to wrap security around every user, every device, every connection — every time. Unify and integrate ...
13:55

Zero Trust Architecture Explained
Zero Trust Architecture is a method of securely designing applications, networks and more as defined by NIST SP-800-207.
17:59

With cyber attacks becoming ever more sophisticated, cyber security has become a very hot topic. In this video, Bob Kalka ...
7:44
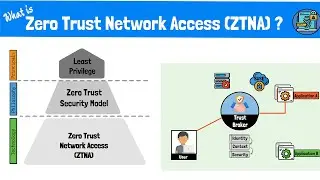
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
Zero Trust Network Access (ZTNA) is a technology that is quickly replacing VPN's as a more secure and scalable way to provide ...
27:54

High level insight into how Cisco provides an holisitc approach to Zero-Trust. More than a product and a platform based approach ...
21:46

Zero Trust Explained | Real World Example
Disclaimer: These are affiliate links. If you purchase using these links, I'll receive a small commission at no extra charge to you.
10:05

Zero Trust - CompTIA Security+ SY0-701 - 1.2
- - - - - The strategy of zero-trust can be a effective way to increase the security of an organization's data. In this video, you'll learn ...
5:47

Zero Trust - простое объяснение главного Security принципа за 5 минут
Что такое Zero trust. Это не фреймворк и даже не библиотека. Это сдвиг мышления. И, наверное, один из главных Security ...
0:43

Zero-Trust Security: Protect Your Business From Cyber Threats!
The future of cybersecurity is here! We break down the critical shift from 'Trust But Verify' to Zero-Trust security. Discover how to ...
57:11

Understanding and Getting Started with ZERO TRUST
John Savill's Technical Training
A look at what Zero Trust really is and how to get started. Looking for content on a particular topic? Search the channel. If I have ...
45:42

Overview of Zero Trust Architectures
In this video we de-mystify and explain recent "Zero Trust” approaches to improve the cybersecurity of enterprise, critical ...
6:30

Zero Trust SD-WAN Solution Overview
Traditional SD-WAN architectures leave security gaps that enable lateral threat movement and expand your attack surface.
2:12

By implementing Zero Trust, you can reduce risk, build trust, and improve protection across your identities, devices, applications, ...
17:12

Zero Trust Network Access (ZTNA) - современный подход к удаленному подключению сотрудников
00:00:00 Почему важно вашим сотрудникам понимать что такое ZTNA 00:00:47 О чем пойдет речь 00:01:09 VPN и его ...
3:02

What is zero trust architecture?
To help councils tackle growing cyber threats, the Local Government Association has released explainer animations on cyber ...
4:39
Zero Trust in 5 Minutes with Brian Deitch
VPNs will never be zero trust because they typically grant broad network access to users, and well, users on the network are a ...
1:47
Best 1.1.1.1 Free WARP VPN to Unlimited Zero Trust! || Tech Wash
The Best 1.1.1.1 Free WARP VPN to Unlimited Zero Trust for Bangladesh is here! In this video, we dive deep into how you can use ...
3:41

Twingate Review: Easiest Zero Trust Network Access in 2024?
➤ CHAPTERS 0:00 - Intro 0:37 - What is Twingate? 0:56 - What is a Zero-Trust security model? 1:43 - Twingate vs Traditional ...
3:56

Zero Trust "Get It" (Official Music Video)
Zero Trust is: Vocalist BJ Allen (Full Scale Riot, Ghidrah, GMK), guitarists Zack Thorne (Bulldoze, Agents of Man, Skarhead, etc.) ...
6:57

Moving to a hybrid, multicloud infrastructure means your resources are also likely scattered throughout multiple IT environments ...